Azure Web Application Firewall
Overview
Azure Web Application Firewall (WAF) is designed to actively shield your web applications from common web exploits and vulnerabilities, such as SQL injection and cross-site scripting.
It operates as an application-level firewall, focusing on web application traffic.
Azure WAF integrates with Azure services like Azure Application Gateway, Azure Front Door, and Azure CDN.
This pack includes
- Log Normalization - XDM mapping for key event types.
Supported log categories
- MMM dd yyyy HH:mm:ss
- yyyy-MM-ddThh:mm:ssEz
- yyyy-MM-ddThh:mm:ssZ
- yyyy-MM-ddThh:mm:ss.E7SZ
For msft_azure_waf_raw, timestamp ingestion is according to the fields below in UTC (00:00) time zone.
- timeStamp
- timeStamp_t
- time
- TimeGenerated
Examples:
- May 03 2025 04:00:00
- 2025-05-03T00:27:53+00:00
- 2025-05-03T00:27:53Z
- 2025-05-02T13:26:25.3391768Z
Time offsets from UTC is supported
See RFC 3339 for more information.
Data Collection
To configure Microsoft Azure WAF to send logs to Cortex XSIAM, follow the below steps.
Prerequisites
Stream Logs Flow
- Sign in to the Azure Portal.
- Navigate to Your WAF Resource:
- To stream Front Door (Global WAF) logs, select the relevant Front Door profile.
- To stream Application Gateway (Regional WAF) logs, select the relevant Application Gateway resource.
- Within the resource, navigate to Monitoring, and select Diagnostic settings.
- Select the log options for the appropriate WAF type:
- Front Door:
FrontDoorAccessLog, FrontDoorWebApplicationFirewallLog
- Application Gateway:
ApplicationGatewayAccessLog, ApplicationGatewayFirewallLog
- Select Add diagnostic setting to create a new integration, or select Edit setting for an existing integration.
- Enter a Diagnostic setting name.
- If you're editing an existing integration, you can't change the name.
- Select the log categories that you want to stream.
Refer to the Log Normalization section for supported log categories for normalization.
- Select the Event Hub streaming method.
- Click the Stream to an event hub checkbox.
- Under Subscription, choose the relevant Azure subscription.
- Under Event Hub Namespace, select the Event Hub namespace.
- Select Save to apply your configuration.
For more information, refer to Microsoft's official Azure Front Door Logs or Azure Application Gateway.
Cortex side
To connect Cortex XSIAM to the Azure Event Hub, follow the below steps.
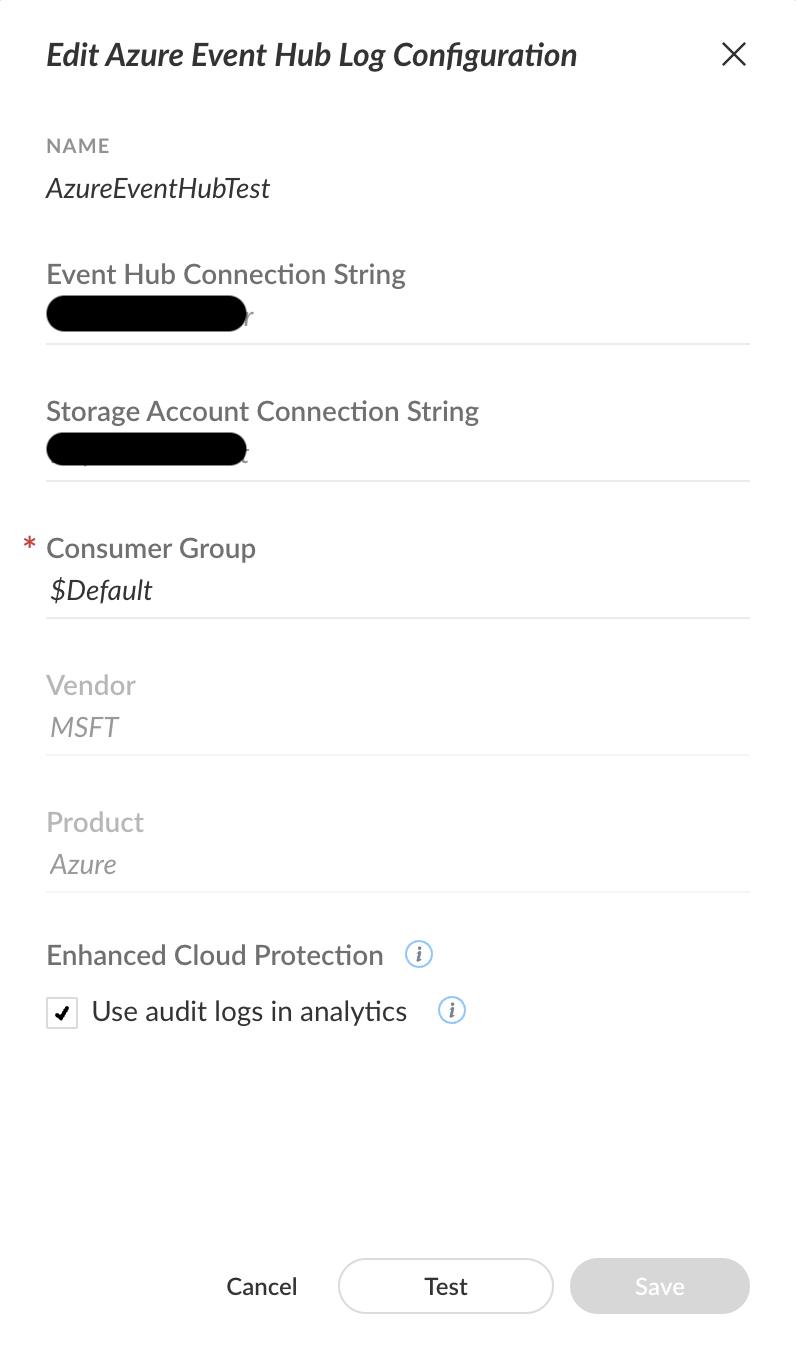
Azure Event Hub Collector
- Navigate to Settings → Data Sources.
- If you have already configured an Azure Event Hub Collector, select the 3 dots, and then select + Add New Instance. If not, select + Add Data Source, search for "Azure Event Hub" and then select Connect.
- Fill in the attributes based on the Azure Event Hub you streamed your data to.
- Leave the Use audit logs in analytics checkbox selected, unless you were told otherwise.
More information can be found here.