This OT Security pack is created to help you to automate the incident response and threat hunting processes in your Operations and ICS environment.
Pack Overview

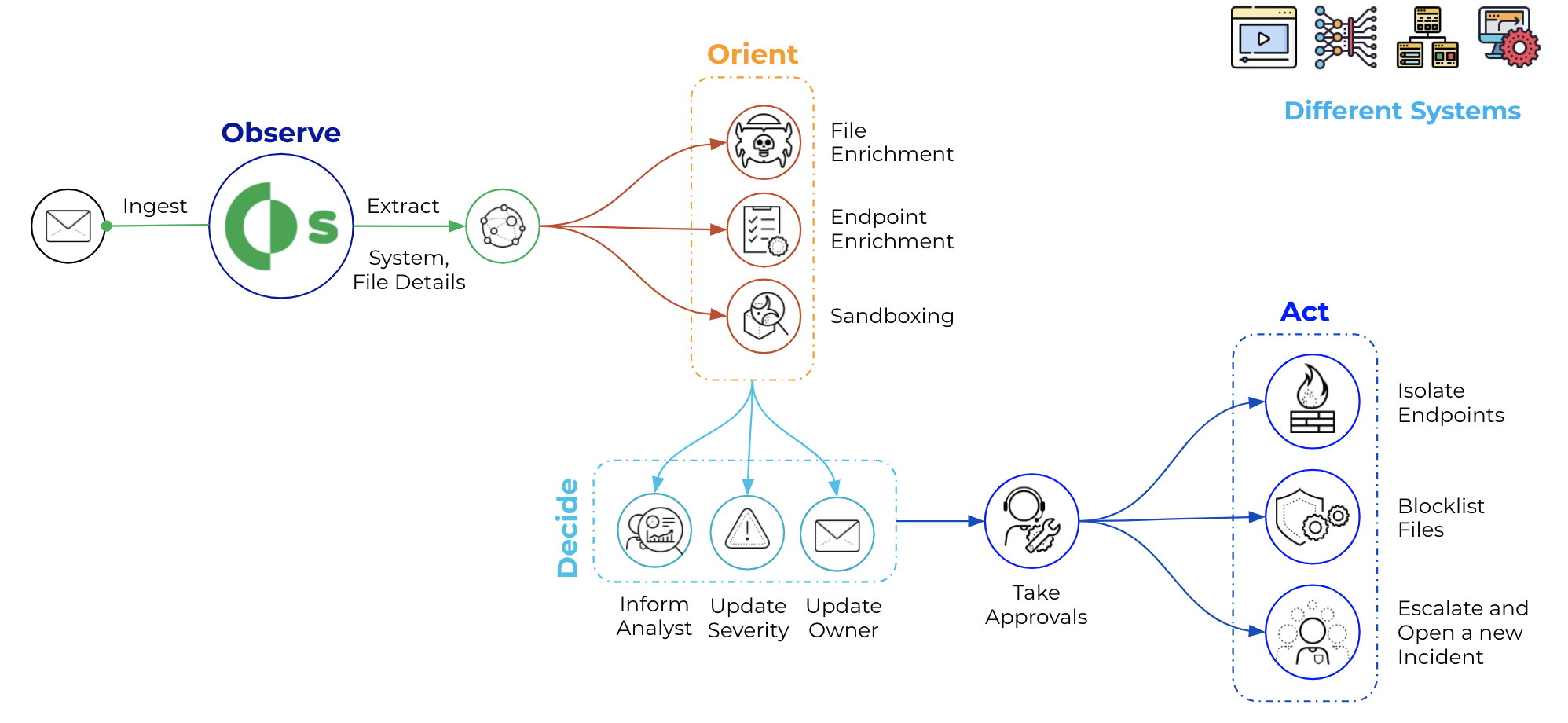
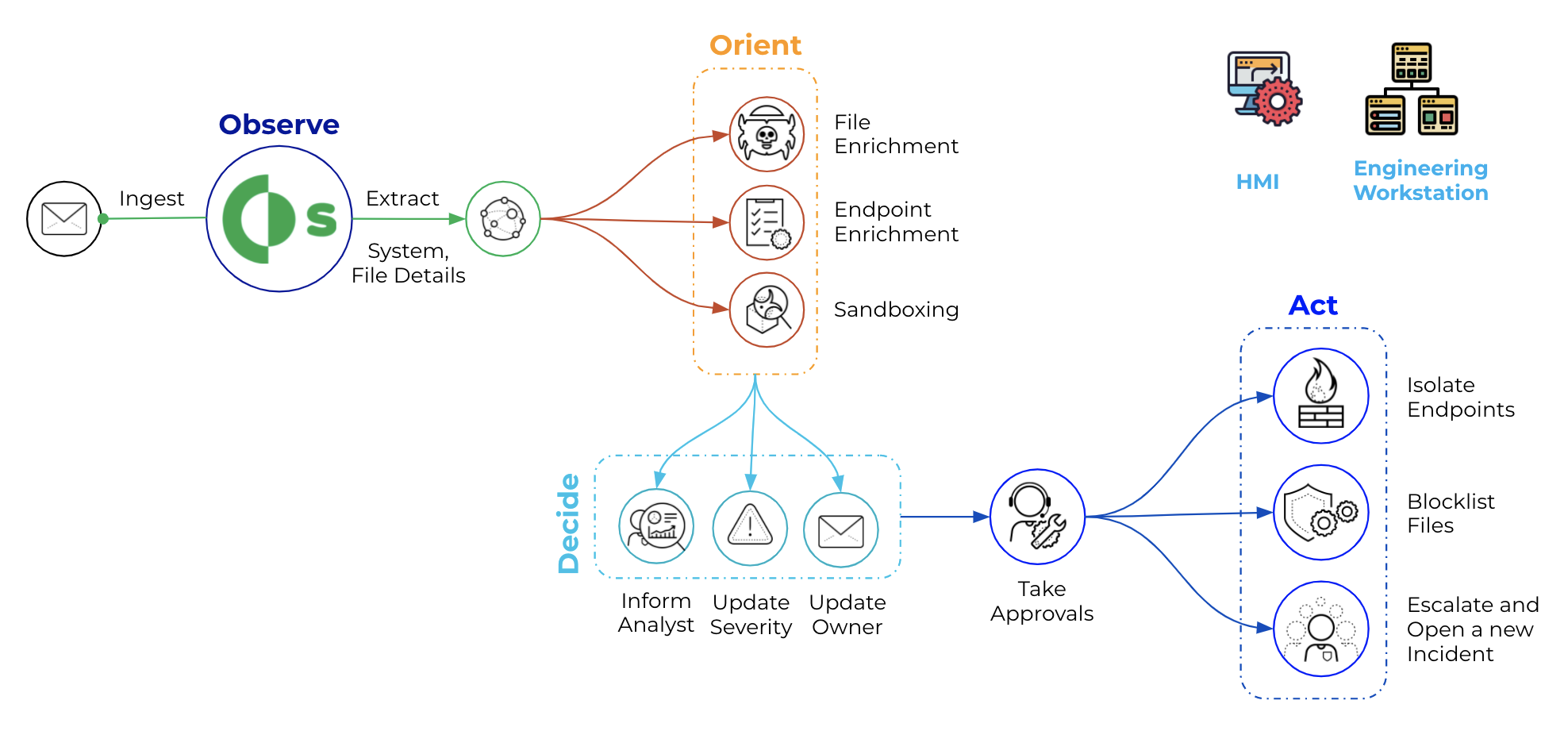
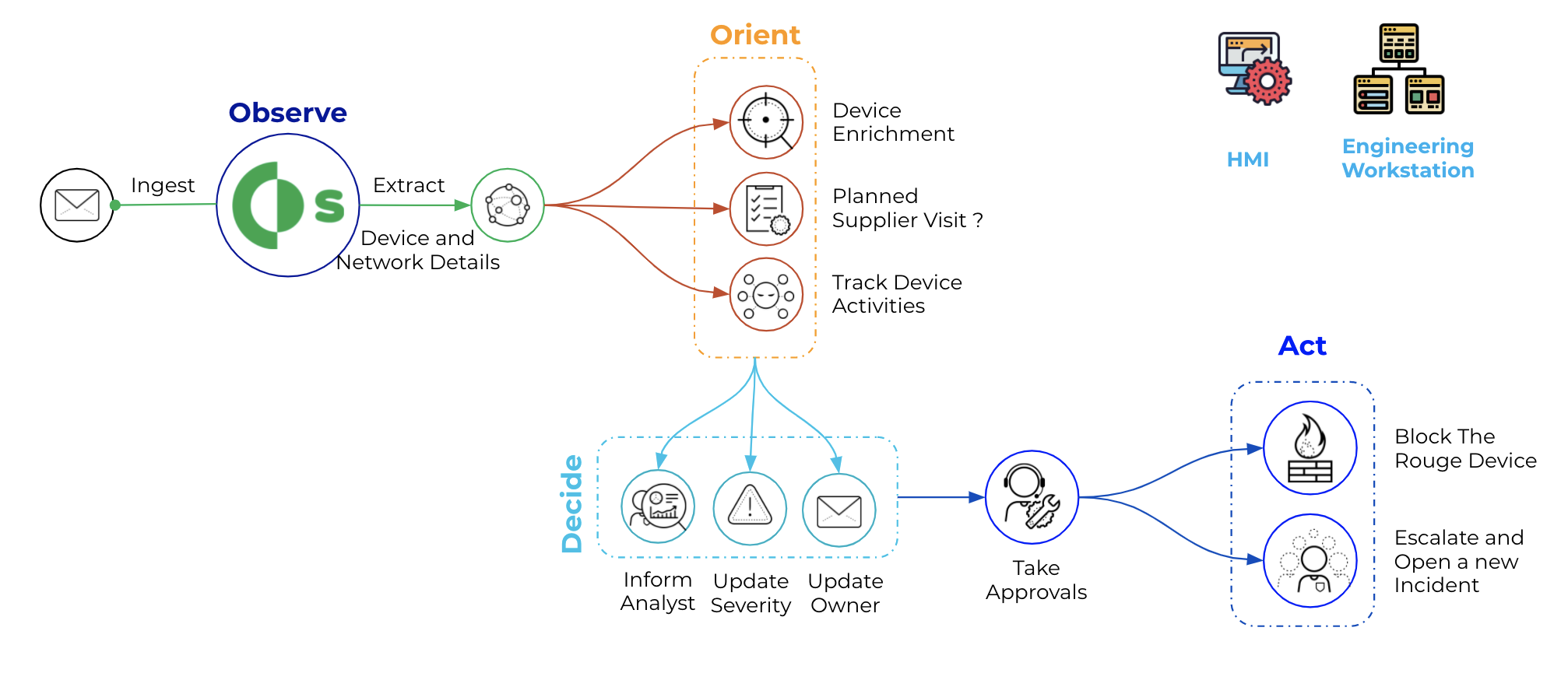
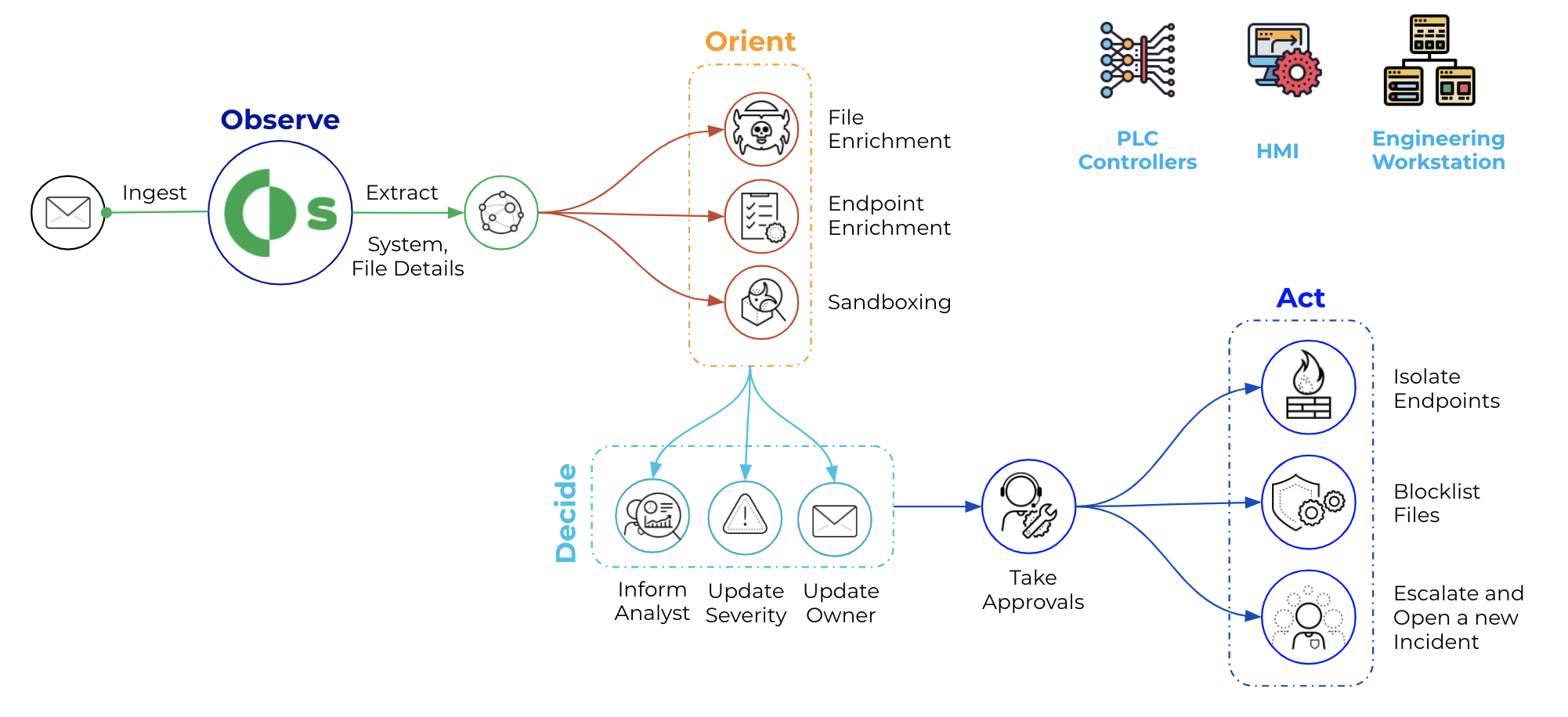
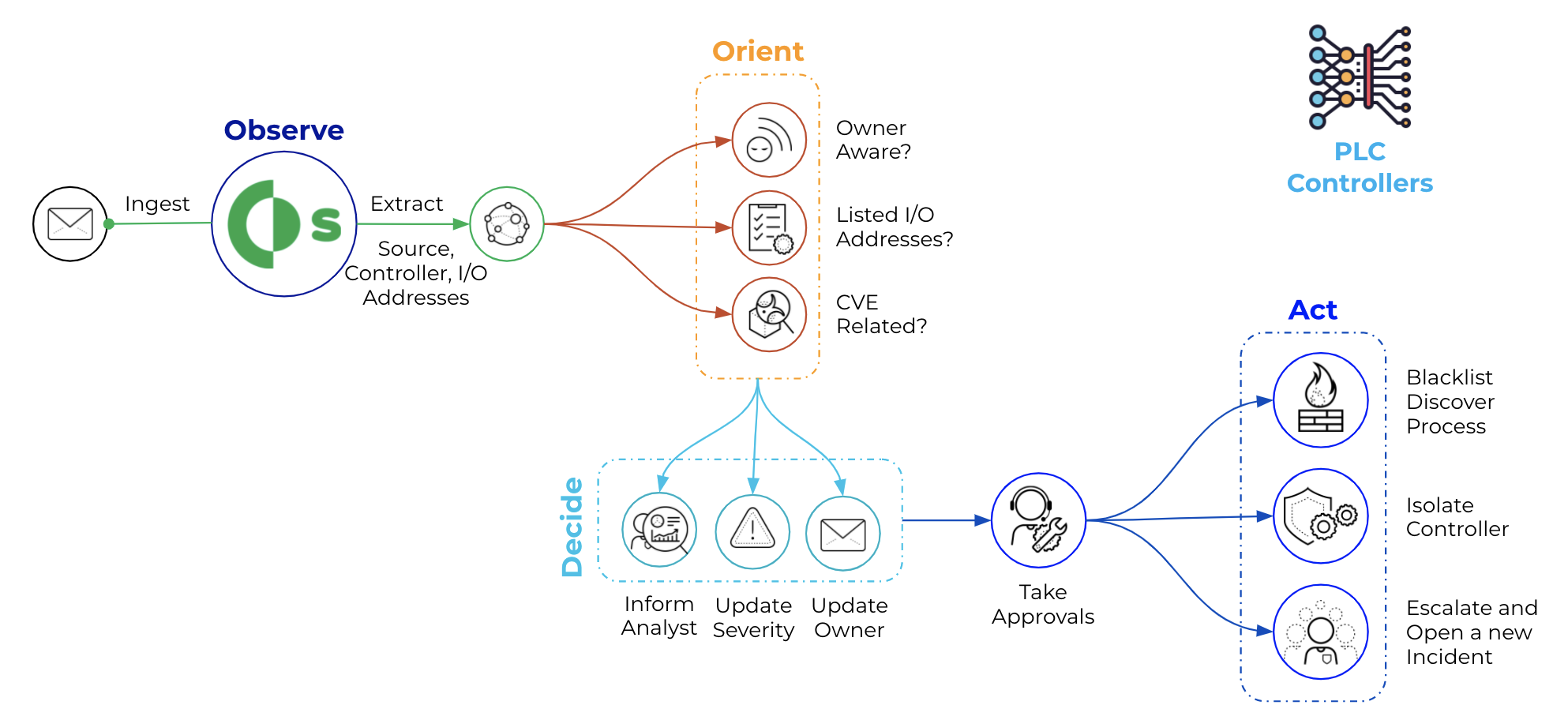
Cortex XSOAR helps to automate OT incidents and alerts response by gathering all relevant data, even from sources that may seem unrelated,
allowing for the buildout of playbooks that cater to the particular automation needs of an ICS’s operational requirements. It also provides bot-aided war rooms where
security analysts and SMEs can safely and securely collaborate on the best course of action. Most importantly, Cortex XSOAR provides automatic documentation of all steps and
processes taken to validate and resolve issues or incidents, creating a knowledge warehouse for first responders.
Pack Roadmap
Below are sample types OT investigation that his pack will focus on:
Initial Access
Supply Chain Compromise

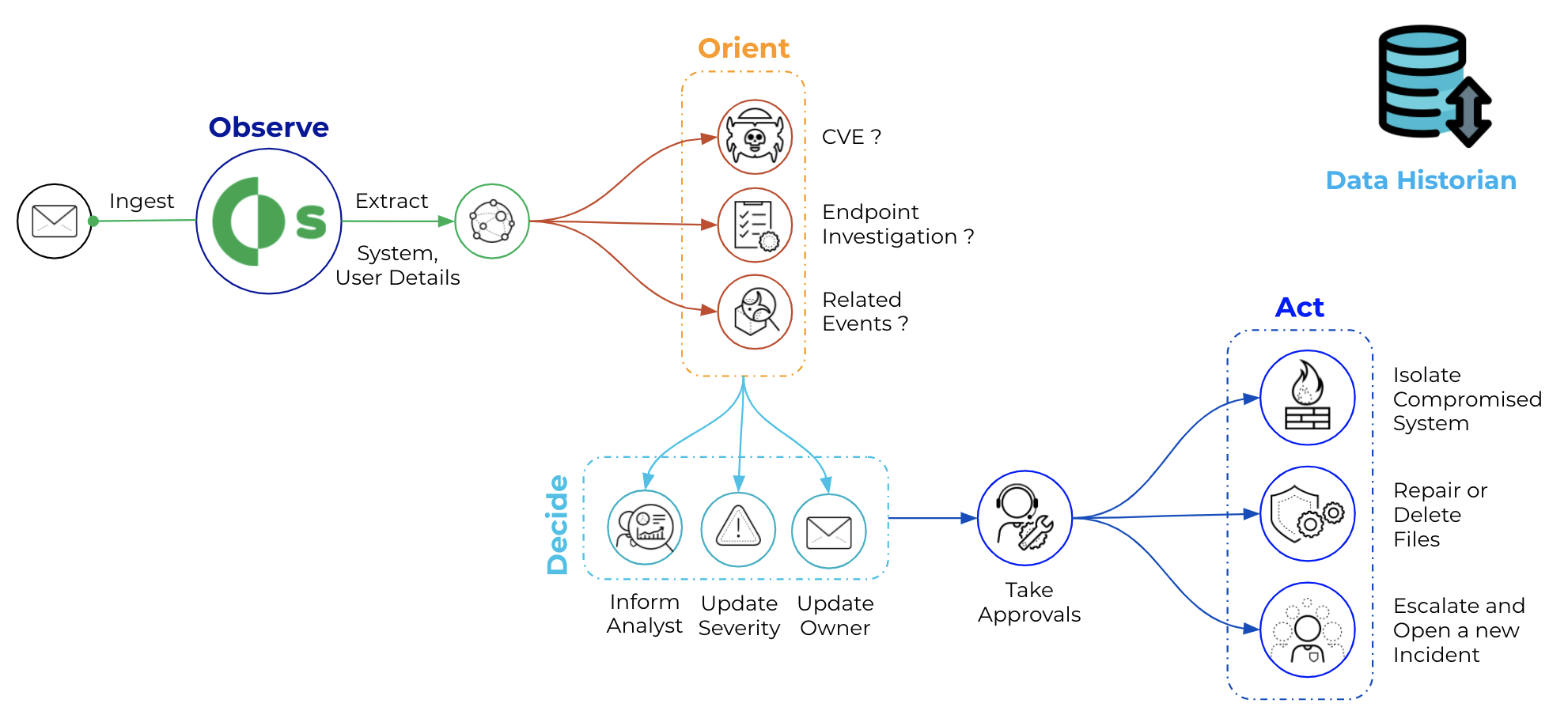
Data Historian Compromise

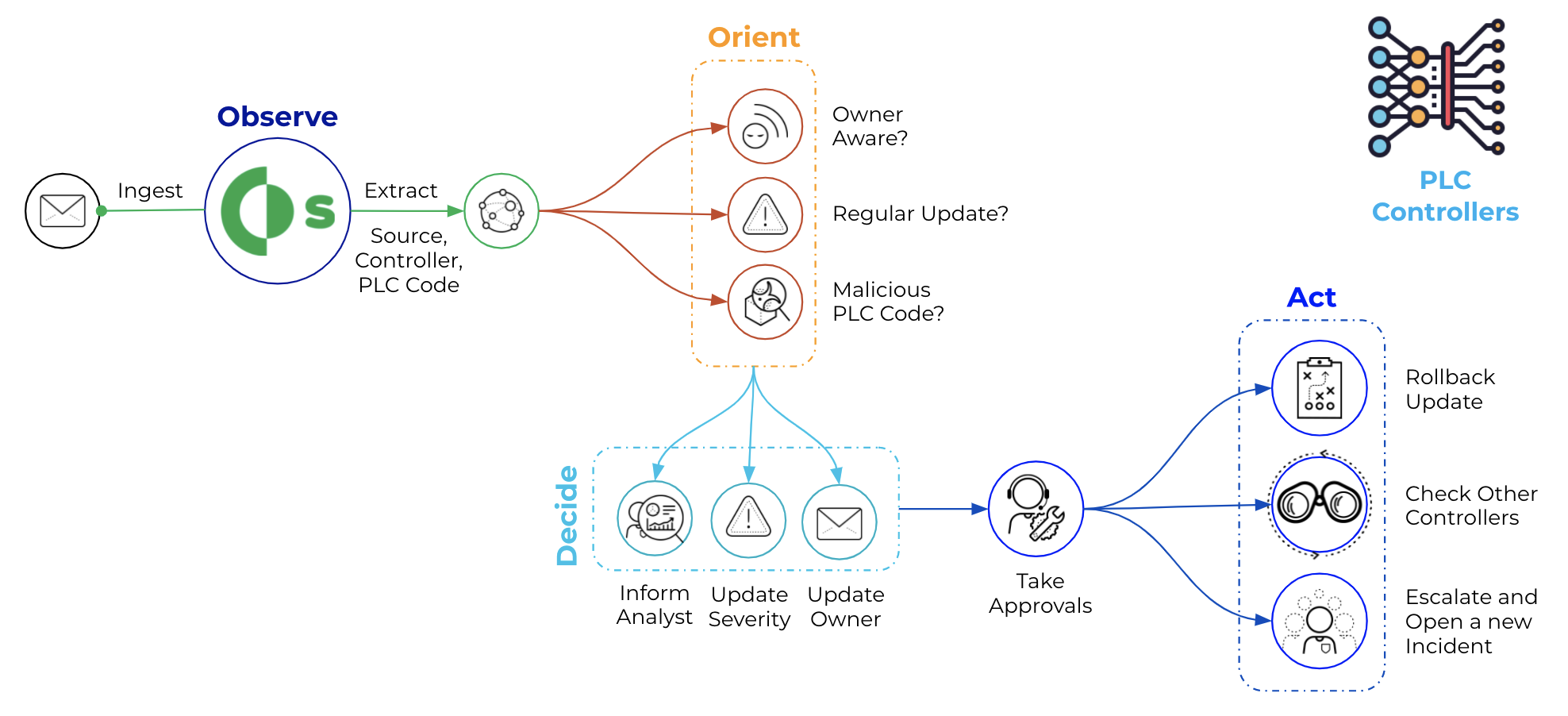
Execution and Persistence
- Unauthorized Program State Alteration

- Project File Infection

- Unauthorized Program State Alteration
Evasion
- Rogue Device Detected

- Rootkits Detected

- Rogue Device Detected
Discovery
- I/O Module Discovery

- Network Service Scanning

- I/O Module Discovery
Lateral Movement
- Default Credentials Login
- Unautherized Remote File Copy
Collection
- Process State Dump
- Unautherized Program Upload
Command and Control
- Proxied Connection Detected
- Protocol Anomaly Detected
Inhibit ICS Function
- Activate Firmware Update Mode
- Unauthorized Program State Alteration
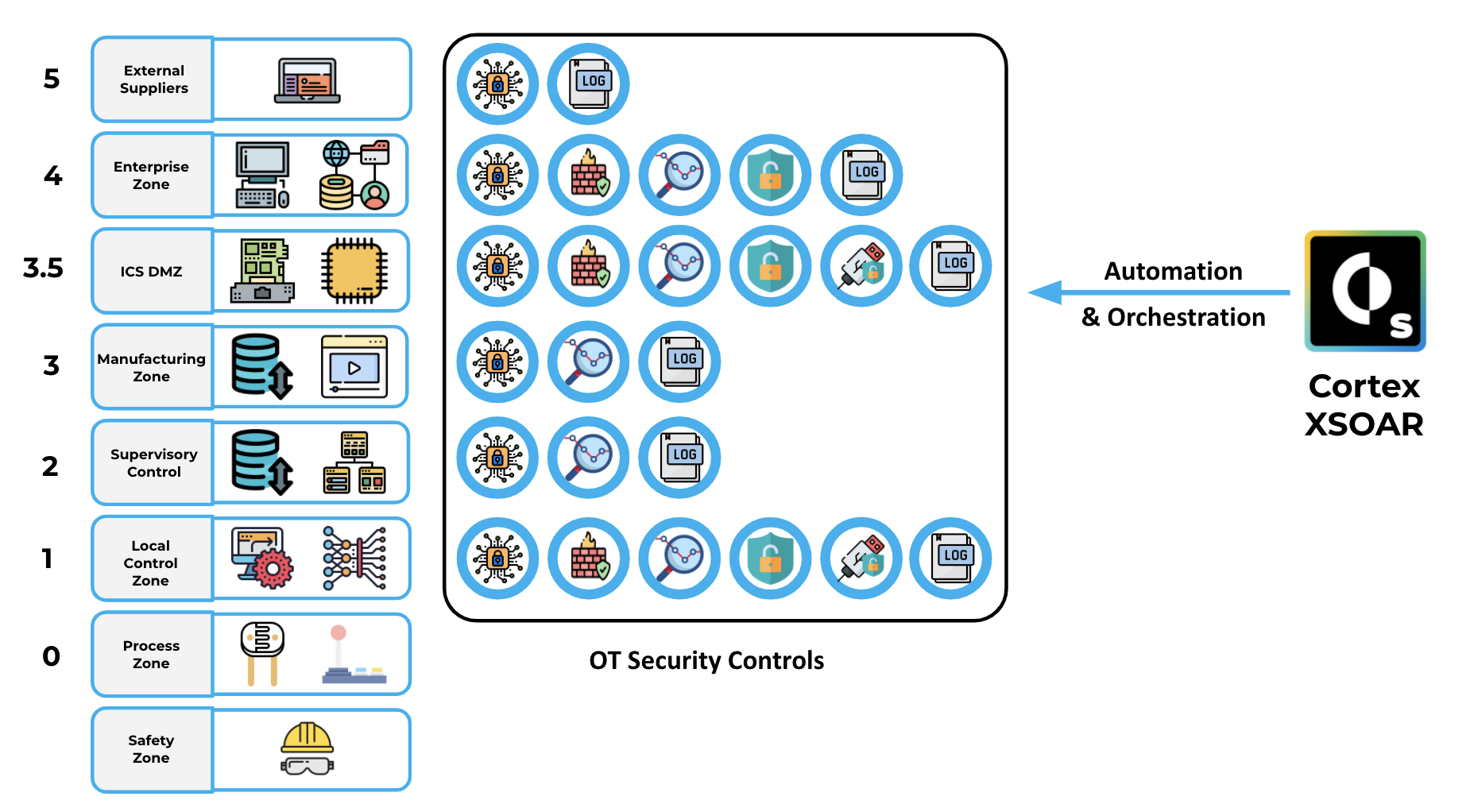
XSOAR content included in this pack will be built based on our integrations with OT security controls that include:
- Network Segmentation Firewalls From
- Palo Alto Networks
- FortiGate
- Cisco
- Calroty
- Network Access Control From
- Cisco
- Forsecout
- Network Visibility From
- Nozomi
- ScadaFence
- Endpoint Security From
- Kaspersky
- Symantec
- SIEM From
- IBM
- Logrhythem
- Splunk
- Vulnerability Management From
- Tenable
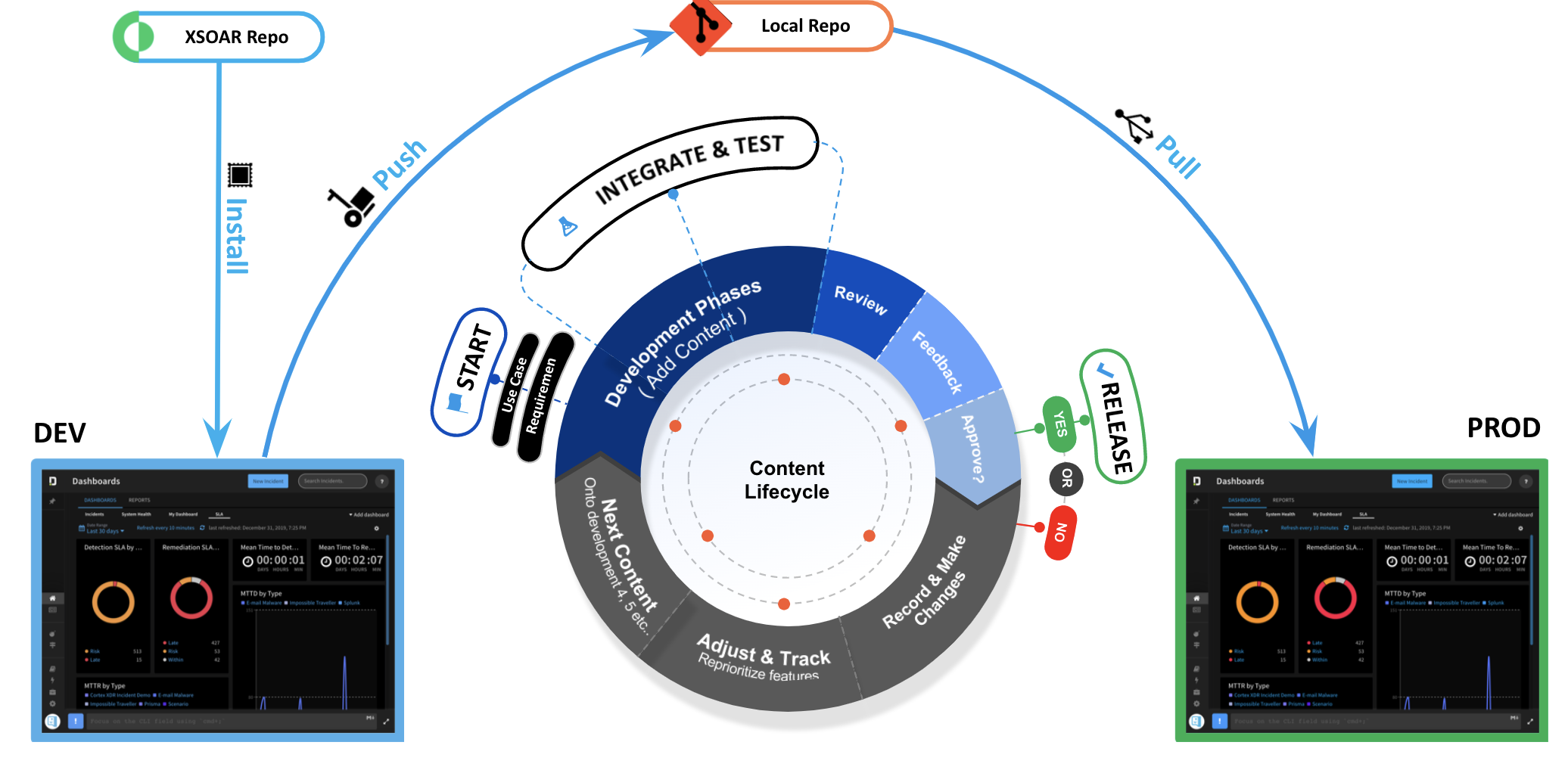
XSOAR in Isolated OT Environment

XSOAR provides the ability to have a production instance running in an isolated OT environment, with a jumb host access to a local repository that stores the content updates, for more details:
Cortex XSOAR 6.13 or Cortex XSOAR 8 Cloud or Cortex XSOAR 8.7 On-prem.