Responding and managing cyber security attacks requires security teams to reconcile data from a variety of different sources. Valuable time is lost shuttling between screens and executing repeatable tasks while an attack continues to manifest.
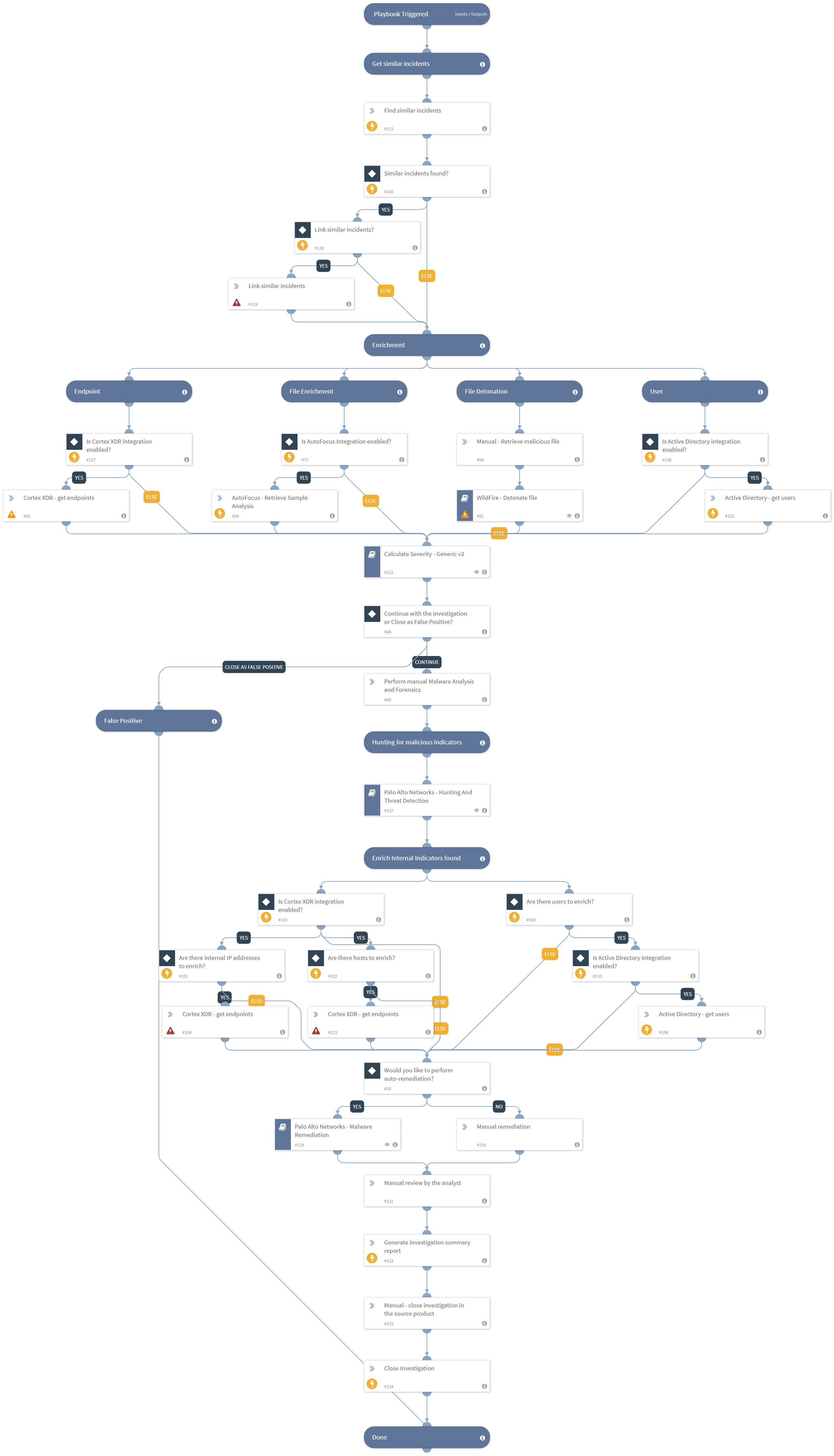
This Palo Alto Networks Comprehensive Investigation content pack contains the ‘Palo Alto Networks - Endpoint Malware Investigation v3’ playbook, that automates response to a malware found on an endpoint, the ‘Palo Alto Networks - Malware Remediation’ playbook, that automates remediation strategies to many different cyber security incidents, and the ‘Palo Alto Networks - Hunting And Threat Detection’ playbook, that automates hunting for other affected entities in your organizations.
The pack also contains the corresponding custom malware incident views and layouts to facilitate analyst investigation.
These playbooks orchestrate across multiple products to extract and enrich IOCs, detonate malicious files, hunt for more IOCs within the organization, and perform remediation using only Palo Alto Networks products.
What does this pack do?
The playbooks included in this pack help you save time and automate repetitive tasks using Palo Alto Networks product integrations:
- Find and link similar incidents
- Extract and enrich all relevant indicators from the source alert
- Calculate severity for the incident based on initial severity provided, indicator reputations, email authenticity check and critical assets if any are involved.
- Hunt for related and affected indicators by leveraging Palo Alto Cortex data received by products
- Remediate the incident by blocking malicious indicators using many different Palo Alto Networks products and techniques.
- Generate an investigation report to document the incident’s details.
As part of this pack, you will also get out-of-the-box incident type views, with incident fields and a full layout. All of these are easily customizable to suit the needs of your organization.
For more information, visit our Cortex XSOAR Developer Docs