This pack has a collection of playbooks to rapidly respond to high profile breaches with existing deployed tools in your enterprise.
The playbooks in this pack can also be used as a template to hunt and block these indicators using additional tools in your environment.
This pack contains the response playbooks for the following breaches:
- Sunburst and SolarStorm Hunting and Response
- FireEye Red Team Tools Investigation and Response
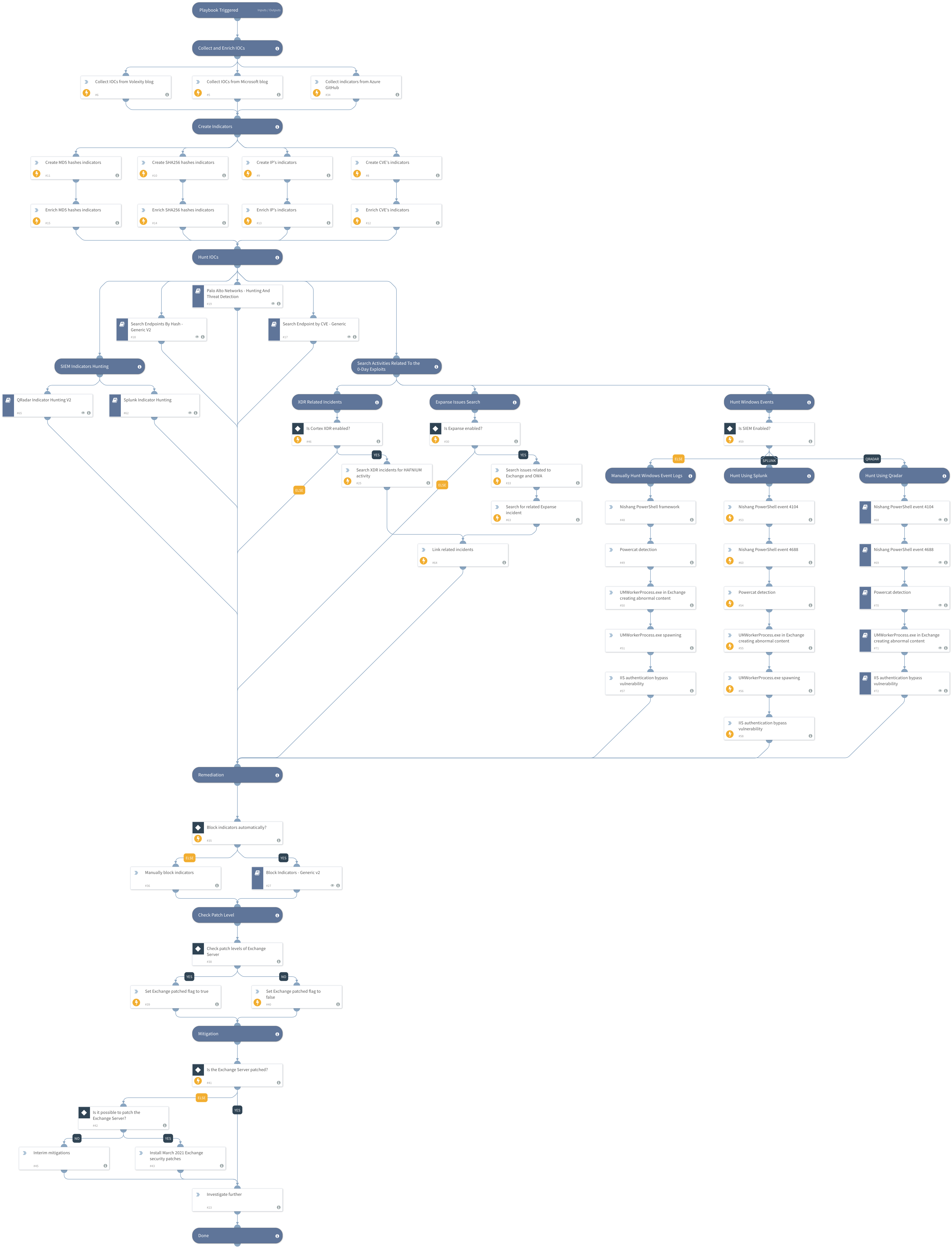
- HAFNIUM - Exchange 0-day Exploits
- Codecov Breach - Bash Uploader
- CVE-2021-22893 - Pulse Connect Secure RCE
- NOBELIUM - wide scale APT29 spear-phishing
- CVE-2021-34527 | CVE-2021-1675 - PrintNightmare
- Kaseya VSA 0-day - REvil Ransomware Supply Chain Attack
More playbooks are available in the following packs:
- CVE-2021-40444 - MSHTML RCE
- CVE-2021-44228 - Log4j RCE
- CVE-2022-26134 - Confluence RCE
- CVE-2022-30190 - MSDT RCE
- CVE-2022-3786 & CVE-2022-3602 - OpenSSL X.509 Buffer Overflows
- CVE-2022-41040 & CVE-2022-41082 - ProxyNotShell
- CVE-2023-23397 - Microsoft Outlook EoP
- 3CXDesktopApp Supply Chain Attack
How to enable it?
- Install the pack.
- Check if the pack has the steps that are relevant to the tools used in your environment.
- Create a job that will run this playbook on a periodic basis.